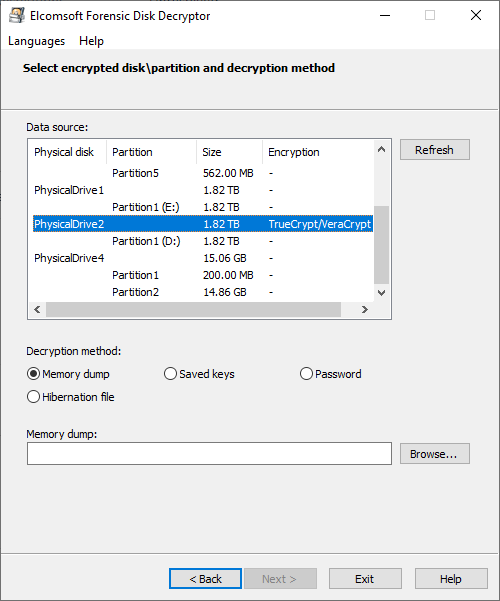
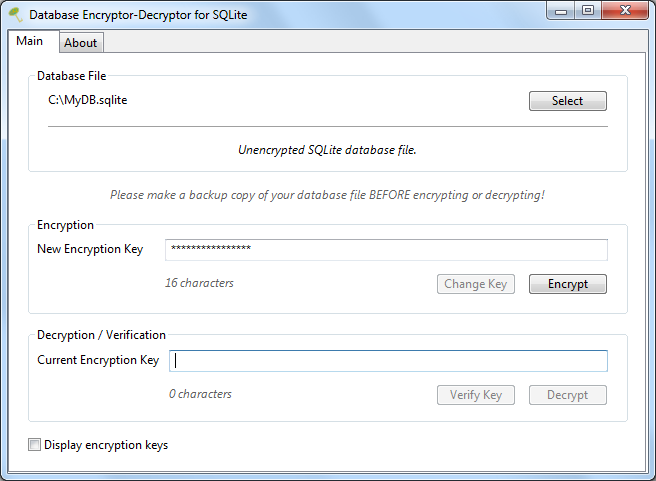
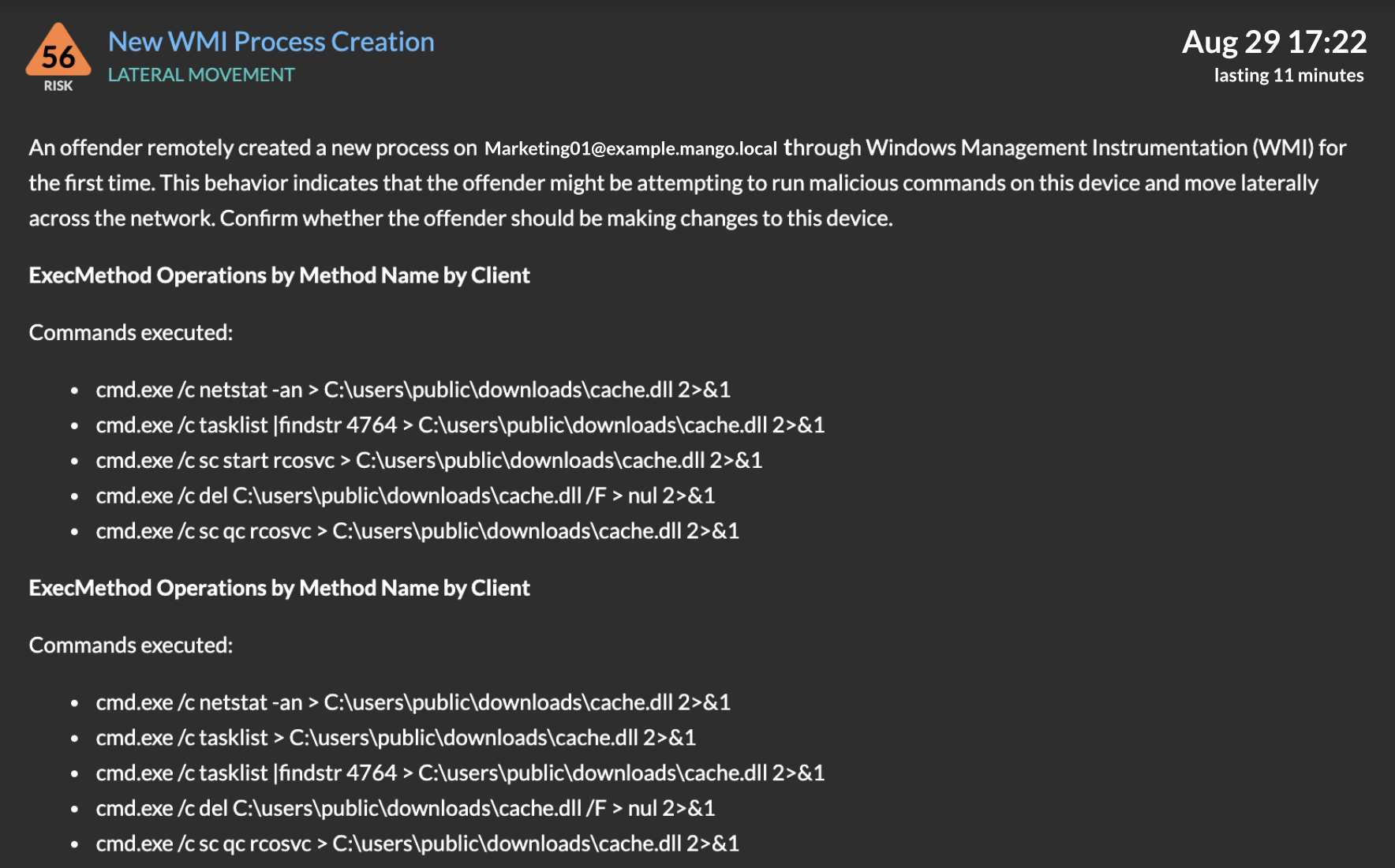
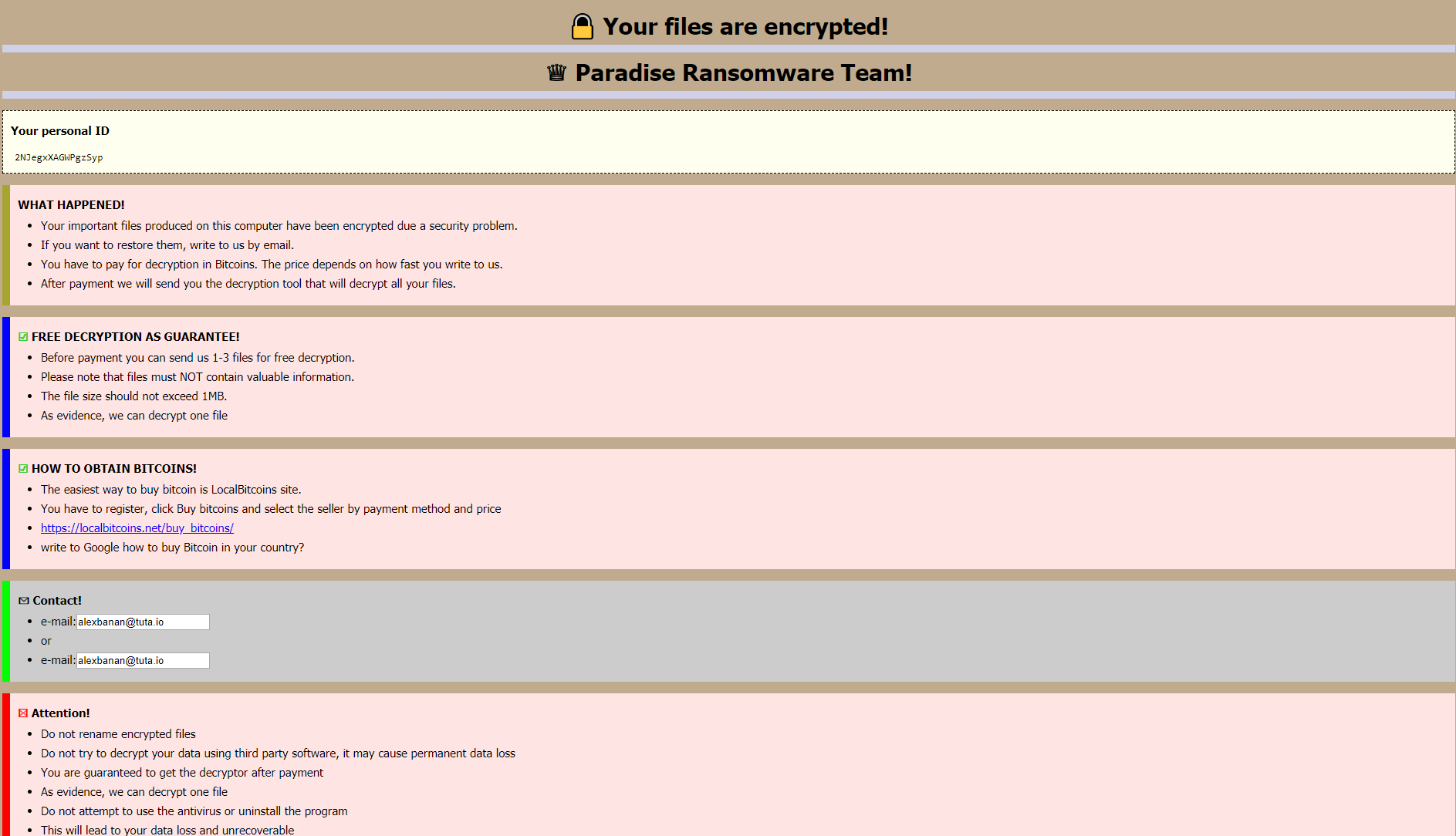
Full disk encrypted drive not booting after putting in decrypt master key check comments : r/ManjaroLinux
Window-and-face objects detection processes: At a server, following the... | Download Scientific Diagram

Copiadora RFID Cloner, programador de llaves, lector de tarjetas, escritor, duplicador, Detector RFID con función de decodificación completa, identificación IC NFC inteligente, iCopy| | - AliExpress

WiFi Full Decode Function Smart Card Key,JOJOCY NFC RFID Card Copier Reader Writer Duplicator for IC ID Cards with 10pcs ID 125khz Cards + 10pcs ID 125kh Keyfobs + 10pcs 13.56mhz IC

Hillstone Networks StoneOS 5.5 R10 Demo: Intelligent Threat Detection in Encrypted traffic. - YouTube